
In today’s increasingly interconnected software development landscape, the security of the software supply chain is more critical than ever. With the growing use of third-party components, particularly open-source libraries, organizations face a significant challenge in ensuring the security of these dependencies. So, to protect the software supply chain, Dependency-Track provides a powerful solution to proactively identify, manage, and mitigate risks.
Challenges in Software Supply Chain Security
Software supply chain security currently suffers from several challenges:
Lack of visibility: Many organizations need help to gain complete visibility into the ALL components they are using, especially those sourced from third parties AI-generated code or open-source projects.
Vulnerability management: Identifying and patching vulnerabilities in third-party components can be slow, exposing organizations to potential attacks.
Inconsistent SBOM usage: Creating and managing a Software Bill of Materials (SBOM) is crucial, but it needs to be implemented consistently.
Complex regulatory compliance: Organizations must adhere to many regulations and standards, such as NTIA’s minimum SBOM elements, CISA’s software supply chain security guidelines and standards from bodies like governments, industry groups or ISO.
Dependency-Track helps solve these problems by providing a comprehensive enterprise platform for managing and securing software dependencies.
Key Features of Dependency-Track To Protect Your Software Supply Chain
1. SBOM Analysis and Management
An SBOM provides a detailed inventory of all the components used in software, allowing organizations to track and manage these components more effectively.
SBOM Ingestion: Dependency-Track can ingest SBOMs generated by external tools, providing insights into the components used in your software and tracking potential risks.
Centralized SBOM Repository: With Dependency-Track, organizations can manage and analyze their SBOMs from a single interface, ensuring consistency across projects and teams.
Compliance with Industry Standards: By analyzing SBOMs against known vulnerabilities and license information, Dependency-Track ensures that organizations adhere to standards like NTIA’s guidelines for transparency and CISA’s recommendations.
2. Vulnerability Management
One of the core strengths of Dependency-Track is its ability to identify and manage vulnerabilities in third-party components.
Real-time Vulnerability Detection: Dependency-Track integrates with various vulnerability databases, such as the National Vulnerability Database (NVD) and OSS Index. This allows it to detect vulnerabilities in real-time, ensuring that organizations are always aware of the risks they face.
Multiple Vulnerability Formats: It supports various formats, such as the Vulnerability Disclosure Report (VDR) and the Vulnerability Exploitability eXchange (VEX), allowing for a flexible approach to vulnerability tracking.
Prioritization: Dependency-Track includes a risk-based approach to vulnerability management. It scores and ranks vulnerabilities based on severity, helping organizations prioritize their remediation efforts.
3. License and Policy Compliance
Managing open-source licenses is critical for ensuring that organizations comply with legal and operational policies.
License Tracking: Dependency-Track continuously monitors the licenses associated with third-party components to ensure that they comply with company policies and avoid legal risks.
Policy Enforcement: Organizations can set policies regarding acceptable licenses, and Dependency-Track will alert them if any component violates these rules.
4. Risk Prioritization
Dependency-Track’s scoring system helps organizations prioritize risks based on the severity of the vulnerabilities and the criticality of the components involved. This allows for efficient allocation of resources to address the most pressing security concerns first.
Scoring System: By assigning risk scores, Dependency-Track helps teams quickly identify high-risk vulnerabilities that require immediate attention.
Use Cases
1. SBOM-Based Vulnerability Scanning
With regulatory bodies like NTIA and CISA increasing emphasis on SBOMs, many organizations now use SBOMs to scan for known vulnerabilities.
Proactive Vulnerability Scanning: Dependency-Track allows organizations to analyze their SBOMs against the latest vulnerability databases, ensuring that any potential issues are identified early in the development lifecycle.
2. Proactive Vulnerability Management
Rather than waiting for vulnerabilities to be reported after the software has been deployed, Dependency-Track enables proactive management by continuously monitoring components.
Example: An organization using Dependency-Track can automatically be alerted when a vulnerability is discovered in one of their dependencies, allowing them to address the issue before it becomes a problem.
3. Policy Enforcement in the SDLC
Dependency-Track integrates seamlessly into the Software Development Lifecycle (SDLC), ensuring that security policies are enforced throughout the development process.
Example: A developer attempts to include a component with a non-compliant license. Dependency-Track will automatically alert the team, preventing the component from being integrated into the software before shipment.
4. Ensuring Open-Source License Compliance
Many organizations rely heavily on open-source software, which comes with its own set of legal obligations. Dependency-Track ensures that all open-source components are properly licensed and compliant with organizational policies.
Overcoming Software Supply Chain Challenges with Dependency-Track
Challenge: Lack of Visibility
Solution: Dependency-Track provides a centralized view of all software components by analyzing SBOMs and continuously monitoring dependencies, ensuring complete visibility into the software supply chain.
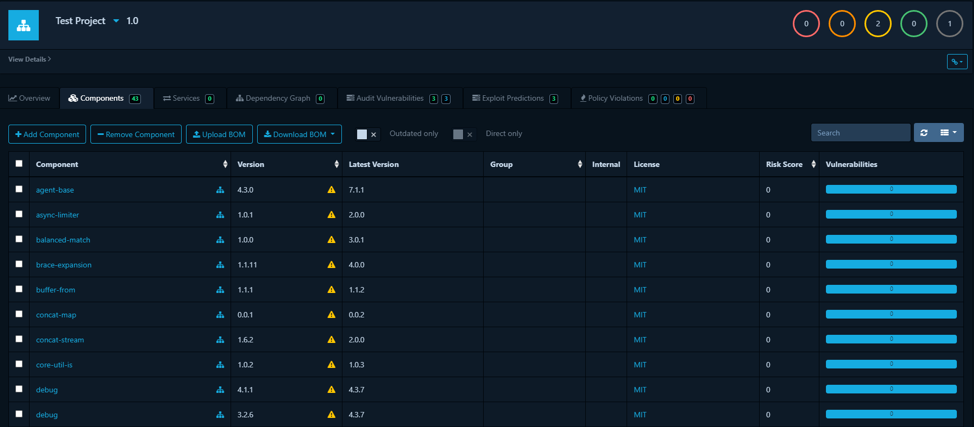
It provides an overview of components in a project, their versions, risk scores, and associated vulnerabilities for quick assessment.
Challenge: Managing Vulnerabilities
Solution: Dependency-Track integrates with multiple vulnerability databases and offers real-time tracking and risk prioritization, enabling organizations to address vulnerabilities swiftly.
Project Vulnerability Dashboard
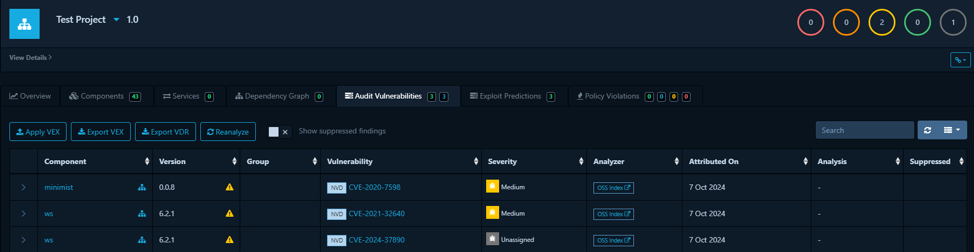
Vulnerabilities identified are shown, like minimist and ws in this diagram, along with their severity ratings, analysis source, and dates.
Vulnerability Audit
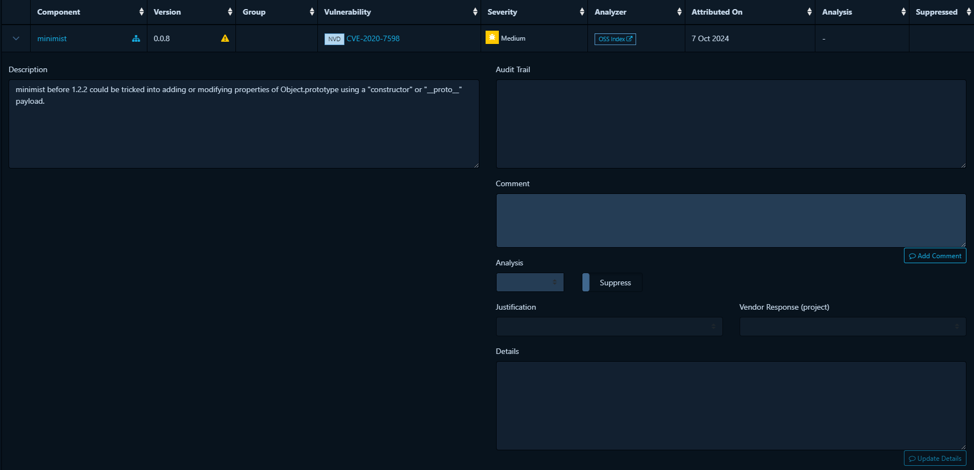
Offers a detailed breakdown of a specific vulnerability, we’re showing it here for the minimist component. It shows CVE details and audit trail options.
Exploit Prediction Scoring System (EPSS)
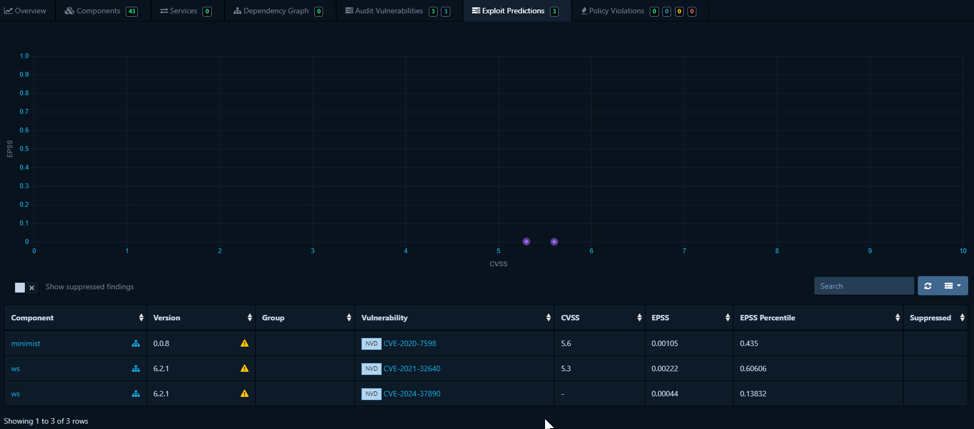
Exploit Predictions displays a graph of vulnerability predictions using CVSS and EPSS scores, helping prioritize remediation efforts based on exploitability.
Analyzers and Vulnerability Sources Integration
Different vulnerability analysis sources can be integrated into the system, including OSS Index, VulnDB, Snyk, and Trivy.
Vulnerability Sources show the available vulnerability sources such as National Vulnerability Database (NVD), GitHub Advisories, and Google OSV Advisories, which are integrated into the system for tracking vulnerabilities.
Challenge: Regulatory Compliance
Solution: By analyzing SBOMs and managing licenses, Dependency Track helps organizations comply with regulations from NTIA, CISA, and others.
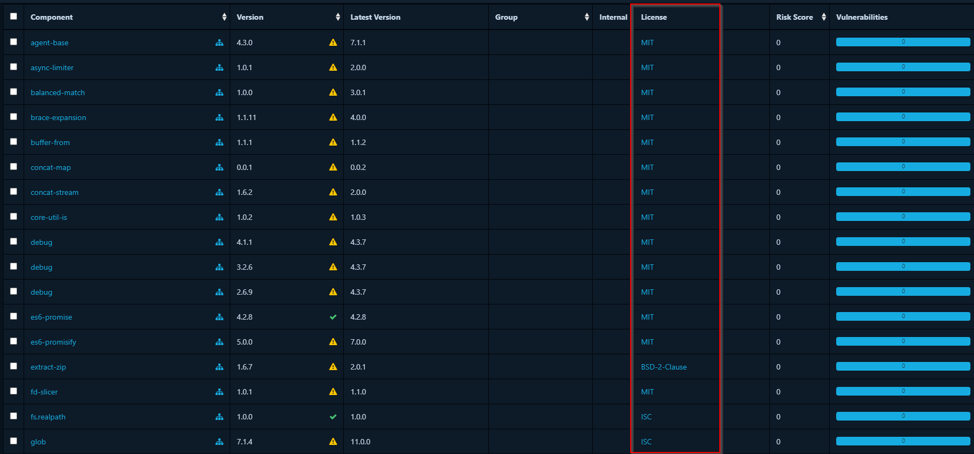 As shown in this diagram, it displays component licenses (e.g., MIT, ISC) for open-
As shown in this diagram, it displays component licenses (e.g., MIT, ISC) for open-
source software, useful for managing compliance and reducing legal risks.
Challenge: Slow Response Times
Solution: Dependency-Track automates the identification and prioritization of vulnerabilities, helping organizations respond to threats faster and more effectively.
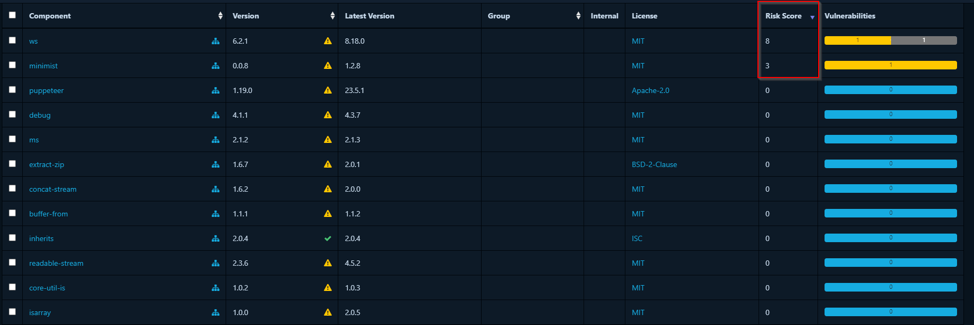 You can see it lists project components along with their risk scores, vulnerabilities,
You can see it lists project components along with their risk scores, vulnerabilities,
and the latest version information, highlighting security risks.
Conclusion
In the evolving software supply chain security landscape, Dependency-Track stands out as a comprehensive solution for managing third-party risks. From SBOM analysis and real-time vulnerability management to license compliance, Dependency-Track helps organizations proactively secure their supply chains and meet industry standards. By integrating Dependency-Track into your DevSecOps pipeline, you can ensure that your software supply chain remains secure, compliant, and resilient against ever-growing threats.
