OWASP®️ Dependency-Track Managed Service
We offer an end-to-end solution to all your SBOM needs from creation through analysis. Our SaaS solution is based on the proven OWASP® Dependency-Track project
Request a DemoImproved Security
Vulnerability Management
Software Audits
Compliance Checks



Why Cryptosoft?
How We Help You
For Developer
For Security Teams
For Procurement Teams
For Executives
Dependency Management
Identify outdated or unnecessary dependencies (components), reducing code size and improving software performance.
Early Vulnerability Detection
Pinpoint potential security flaws and ensure license compliance within components during development, allowing for proactive mitigation.
Simplified Open-Source Compliance
Manage open-source license obligations with ease, avoiding legal complications down the line.
Examples of typical client use cases
What is a software supply chain?
A software supply chain encompasses anything and everything that touches an application as it is being developed; the component code, how the components are connected, security, development processes, deployment processes, tools used etc. It is the end-to-end story of assets, processes and tools being used in the creation of a software product.
What is an SBOM?
A “software bill-of-materials” (SBOM) defines the complete inventory of software components and their dependencies in an application. It is defined in JSON text and follows a standard format. SBOMs have emerged as a key building block in software security and software supply chain risk management as they provide visibility into all the components in the chain and their dependencies.
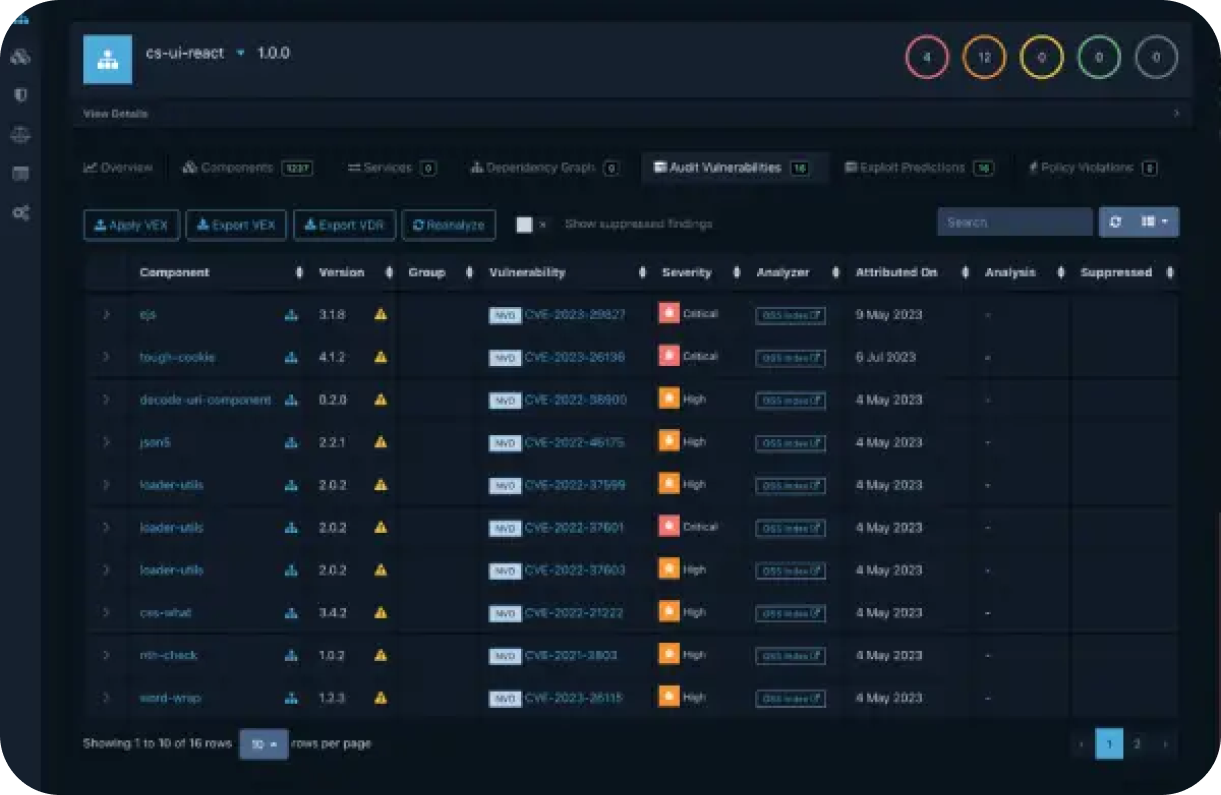
What is OWASP Dependency-Track and why should I use it as part of my security strategy?
OWASP Dependency-Track (D-T) (https://owasp.org/www-project-dependency-track/) is an open source project that has been evolving since 2013. It is an intelligent component analysis platform that allows organizations to identify and reduce risk in the software supply chain by analyzing risks in SBOMs. D-T analyzes components used in the SBOM for security vulnerabilities, license compliance and software pedigree.